Chezie Security Handbook
A comprehensive document of all of our security practices.
Written By Toby Egbuna
Last updated 8 days ago
Documentation
Access Control Policy
Asset Management Policy
Incident Response Plan
Data Classification Matrix
Business Continuity and Disaster Recovery
Data Flow Diagram
Third-Party Integration Sequence Diagram
Data Management Policy
Third-Party Management Policy
GDPR Compliance Policy
Human Resource Security Policy
Risk Management Policy
Information Security Policy
SOC2
Change Control
Privacy and Data Protection
Business Information
Company Name
Dyversifi Inc.
Name of product, service
Chezie for ERGs.
Do products, services, or systems require network connectivity between parties?
Yes.
Do the products, services, or systems require remote access between parties?
No.
Products, services, or systems that require system-to-system integration?
Yes. Integrations to your
Video meeting software (i.e. Zoom, MS Teams, or Google Meet)
Chat software (i.e. Slack or MS Teams)
Calendar (i.e. Google or Outlook Calendar)
Are technology or software applications provided?
Yes.
List the names of the applications provided that are in scope.
Chezie.
Technology or software is being provided?
Commercial Off-The-Shelf.
Hosting Model included as part of this service.
DigitalOcean
Type of Cloud Computing service(s) provided.
Software as a Service.
Company website URL
Enterprise Risk Management
Is there a formalized risk governance plan approved by management that defines the Enterprise Risk Management program requirements?
Yes there is a formalized risk governance plan.
Does the risk governance plan include risk management policies, procedures, and internal controls?
Chezie’s Risk Governance Plan is guided by procedures and our risk management policy. Please see Risk Management Policy
Is there a documented third-party risk management program in place for the selection, oversight and risk assessment of third parties (e.g., subcontractors, suppliers, service providers, dependent service providers, sub-processors) in scope for the services?
Currently, we do not have a third-party risk management program, but we have plans to implement one in the near future.
Are annual internal risk assessments performed?
Yes. All annual risk assessments are performed in-house.
Does your organization maintain an internal risk register for tracking and remediating risks?
As part of our risk governance plan, we maintain an internal risk register.
How often is the risk register reviewed internally?
We review our risk register annually.
Information Security Policy
Is there a set of information security policies that have been approved by management, published, and communicated to constituents?
Yes, please see Information Security Policy.
Do the information security policies and procedures establish requirements for the protection of information that is processed, stored or transmitted on external systems?
The information security policies and procedures establish requirements for the protection of information. We follow industry-standard best practices to ensure all information we handle is done so with security in mind.
Have all information security policies and standards been reviewed in the last 12 months?
All information security policies have been reviewed in the last 12 months.
Asset and Information Management
Asset Management Program
Where is client data stored geographically
DigitalOcean West Region, DigitalOcean East Region (backup).
Do you logically and physically segregate production and non-production environments? How do you ensure Production Data is not to be replicated or used in your test environments?
There is a logical and physical disassociation between local environments and remote environments. Our data models are built before a line of code is written so we're able to develop locally with dummy data that matches (in shape) to the data that lives in our servers.
Personnel Security
Is there an acceptable use policy for information and associated assets that has been approved by management, communicated to appropriate constituents, and assigned an owner to maintain and periodically review the policy?
Please refer to our Information Security Policy. This policy is regularly reviewed and updated.
Are all employees and contractors required to acknowledge/sign your organization's acceptable use policy upon hire?
Yes.
Is required annual information security awareness training completed by all organization personnel?
Yes, we require all employees and stakeholders to complete information security awareness training.
Physical and Environmental Security
Is there a physical security policy approved by management, communicated to constituents, and has an owner been assigned to maintain and review?
Data is housed with DigitalOcean, they are an industry leader in physical data storage. DigitalOcean writes and implements best practices.
Can your organization's constituents physically access scoped data for this engagement?
No, all of the data lives in the cloud (DigitalOcean)
Is authentication required for physical access to scoped data?
Physical access is not possible.
Change Management
Is there an operational Change Management/Change Control policy and process that has been documented, approved by management, communicated to appropriate personnel and assigned an owner to maintain and review the policy?
Yes, please refer to our Change Control Policy.
Access Control
How does Chezie access a client’s data?
All data collected by Chezie is explicitly provided by the user through the use of online forms or with user permission through third-party integrations.
Does Chezie get access to a client’s system to provide a service?
Chezie will not access a client’s system to provide service. If a client gives Chezie access to any system it will only be to gather data relevant to Chezie’s data model. Chezie does not blindly scrape proprietary/sensitive data.
Will data Chezie collects be transferred to other region(s)?
In compliance with Chezie’s backup policy, currently, any data moved to another region will be restricted to safeguard data from a centralized disaster or critical event.
Are Chezie’s employees and contractors able to access scoped data?
Chezie’s employees are instructed not to access scoped data unless explicitly asked to by relevant stakeholders or for blind testing purposes and to explore anomalies.
Are unique IDs required for authentication to applications, operating systems, databases and network devices.
Yes, unique IDs are required for authentication purposes.
Does Chezie’s password policy require keeping passwords confidential?
Yes.
Is Multi-factor Authentication required in order to access scoped data?
Yes.
Is there a process for reviewing access?
We limit IAM permissions and access to a select group of people and limit permissions to the lowest possible level. We regularly review access permissions.
Are Access privileges revoked when an employee is terminated?
Yes. We make the adjustment within 24 hours of the employee’s termination.
Application Security and SDLC
Are applications used to transmit, process or store scoped data?
Yes, applications are used to transmit and process data.
Do you follow a Secure SDLC methodology, please describe. Please include a description of your SDLC methodology. You may provide the table of contents for your Secure SDLC procedure.
We currently adhere to SLDC, we plan on integrating the security aspect of this by associating annual pen testing before deployment of our V2 dashboard coming out in early 2023.
Our Process:
Design
Development
Testing
Deployment and Maintenance
Cybersecurity Incident Management
Is there an established Cybersecurity Incident Management Program that has been approved by management, communicated to appropriate constituents and an owner to maintain and review the program?
Yes.
Is there a formal Incident Response Plan that includes an escalation procedure?
Are events on Scoped Systems or systems containing Scoped Data regularly reviewed and monitored to uncover potential incidents?
Through regular maintenance of our firewall and restricted network access, we limit IAM permissions and access to a select group of people. We monitor data coming into our servers regularly, identify unusual traffic, and log and patch any bugs.
Is there a staffed form of communication (e.g., e-mail, web form, phone, etc.) available to customers/clients 24/7/365 to report security incidents?
Yes. All issues can be communicated in-app or to support@chezie.co.
Contingency Planning - BCP & DR
Are formal business continuity procedures developed and documented?
Please refer to our business continuity and disaster planning.
Is there a formal, documented Information Technology Disaster Recovery exercise and testing program in place?
Yes.
Are there any dependencies on critical third-party service providers?
Yes, DigitalOcean has daily snapshots of our DB. These DB images are accessible and stored securely on the cloud.
Has the organization established processes for third-party service providers to provide immediate notification in the event of a disruption that impacts delivery of the products and/or services they provide?
Immediately. We have a response point person that will notify in the event of a breach. We will contact affected partners through email, Slack, text, phone (through as many mediums we have at our disposal).
Is there a policy or process for the backup of production data?
Yes. 3-2-1 Backup strategy. 3 copies of data, two backups. Two different DigitalOcean DB services, 1 copy of data in a different region.
Is scoped data backed up and stored offsite?
Yes.
What is the location (entity name and location) of any backup site(s)?
DigitalOcean - NYC1 - New York City, United States
Is there a formal process focused on identifying and addressing risks of disruptive events to business operations?
Yes.
Is there a data retention policy or process with a retention schedule?
Generally, we keep data for as long as it is relevant. A company can request data deletion at any point.
**Subject to change
Endpoint Device Security
Are End User Devices (Desktops, Laptops, Tablets, Smartphones) used for transmitting, processing, or storing scoped data?
All transmission, processing, and storing of scoped data is done on DigitalOcean.
Are there documented end-user device security configuration standards?
Every device must be secured with anti-virus protection, and employees are not allowed to use unsecured networks with devices that access company data. We require employees to always keep their OS's up to date and download the latest security patches. Employees are not allowed to download illegal or pirated content with devices used to access company data.
Are there documented end-user device security configuration standards?
Is there a mobile device management program in place that has been approved by management and communicated to appropriate constituents?
Are non-company-managed computing devices used to connect to the company network and store scoped data?
No, none of the above.
Server Security
Are End User Devices (Desktops, Laptops, Tablets, Smartphones) used for transmitting, processing or storing Scoped Data?
Yes, servers are used for transmitting and processing Scoped Data.
Are server security standards reviewed and/or updated at least annually to account for any changes in environment, available security features and/or leading best practices?
Yes, we regularly review our server security standards and apply any patches or updates as available and necessary.
Are all unnecessary/unused services uninstalled or disabled on all servers?
Yes, all unnecessary/unused ports, services, and whitelists are disabled on our servers.
Are vendor default passwords removed, disabled, or changed prior to placing any device or system into production?
Yes, Chezie does not keep default passwords.
Are all systems and applications patched regularly?
Chezie patches systems as patches become available.
Are there any Operating System versions in use within the Scoped Services that no longer have patches released? If yes, please describe in the Additional Information section.
Currently, Chezie does not use unserviced/unmaintained OS versions.
Is there an anti-malware policy or program that has been approved by management, and communicated to appropriate constituents and an owner to maintain and review the policy?
Every device must be secured with an anti-virus, employees are not allowed to use unsecured networks with devices that access company data, we require employees to always keep their OS's up to date and download the latest security patches. Employees are not allowed to download illegal or pirated content with devices used to access company data. Coupled with some other of our device policies and education surrounding the engagement of dubious profiles in social media, dubious text messages, and dubious emails and URL links.
What measures do you take to ensure your APIs are secure?
Accessed through a short-lived JWT associated with a refresh token. We limit the depth and rates that users can hit our API.
Please describe the detection and protection technologies in place to identify anomalies in the corporate and production environment.
We currently use CloudWatch anomaly detection to look for a detect for anomalies.
Certificate Management
Chezie uses AWS certificate manager, which automates the process of renewing our SSL/TLS certificates and keys. (AWS is used for domain management and related operations).
Encryption Standards
Chezie uses DigitalOcean’s MongoDB services which are encrypted at rest. In transit data travels through SSL.
Network Security
Is there a policy that defines network security requirements that is approved by management, communicated to Constituents, and has an owner to maintain and review?
Yes. All networks must be secured with a strong password and updated with the latest security updates.
Are there security and hardening standards for network devices, including Firewalls, Switches, Routers and Wireless Access Points (baseline configuration, patching, passwords, Access control)?
Is there a policy that defines the requirements for remote access from external networks to networks containing Scoped Systems and Data that has been approved by management and communicated to constituents?
Yes.
Are encrypted communications required for all remote network connections from external networks to networks containing Scoped Systems and Data?
Yes.
Are Network Intrusion Detection/Prevention capabilities employed e.g., appliance, software, etc.?
Yes, we employ firewall(s) as a preventative mechanism.
Is there a DMZ environment within the network that transmits, processes or stores Scoped systems and data e.g., web servers, DNS, directory services, remote access, etc.?
No DMZ environment is currently in place.
Is there a wireless policy or program that has been approved by management, communicated to appropriate constituents and an owner to maintain and review the policy?
Encrypted connections
All of our traffic goes over SSL/TLS.
Threat and Vulnerability Management
Is there a documented vulnerability management policy or program that has been approved by management, communicated to appropriate constituents and an owner assigned to maintain and review the policy?
Chezie’s VMP can be summarized as:
Assess our Assets
For vulnerabilities
Prioritize vulnerabilities
Assign Value
Gauge threat exposure
Add threat context
Act
Reassess
Improve
In this vein, we attempt to identify threats before we have incidents,
improve processes, and follow best practices.
Has your organization implemented scanning tools to identify any software vulnerabilities on systems in the organization?
We use Nmap to target our infrastructure resources (server(s), db, buckets [spaces]) and automatically scan for vulnerabilities.
How often is vulnerability scanning performed for systems that process or store Scoped Data?
Scanning is performed daily.
Does the organization maintain policies, standards and procedures for identifying and managing supply chain risks (i.e. ensuring software and hardware components used as part of delivering a service or product do not present a risk)?
Yes.
Does your organization perform annual penetration testing?
Find a copy of our latest penetration report below. Please note that we are working on the DNS records that would bring our grade to an “A.”
Patch Strategy
For non-production, we simply keep all of our devices and OS's up to date with the latest versions and use them in only secure networks. For production we scan our DigitalOcean Droplets for applicable OS patches, identify patches, group instances at a suitable time and report patching compliance across the server environment.
Ransomware Prevention
We utilize the following:
Data backups
Regular system maintenance and up keep firewalls ,
Endpoint security
on access to our production server
Team training on suspicious activities that have led to opening access to strangers, no useless network/port access
Baseline Practices
In addition to the aforementioned, we disable unused networks and services, regularly audit and modify network rules and access privileges, and reconfigure our network firewall as needed.
Compliance and Operational Risk
Are there policies and procedures to ensure compliance with applicable legislative, regulatory and contractual requirements?
Yes, we have a suite of policies that adhere to all applicable compliance regulations.
Is there an internal audit, risk management, or compliance department, or similar management oversight function with responsibility for tracking the resolution of outstanding regulatory or compliance issues?
Chezie contracts a third-party auditor to look over all of our regulatory policies and practices to ensure all of our policies and standards meet compliance where we operate.
Is there a compliance program or set of policies and procedures in place to restrict activities or transactions for sanctioned countries (e.g., country blocking)?
We do not work with sanctioned countries.
Are documented policies and procedures maintained to enforce applicable legal, regulatory or contractual cybersecurity compliance obligations?
See responses COR1 (Compliance and Operational Risk) and COR2
Third Party Sub-Processors
Third-Party Integrations
What are they?
Third-party application integrations are those that we use to make a Chezie user’s life easier. We create applications on platforms like Slack and Microsoft Teams and Chezie user’s leverage them to enhance their user experience.
What do you use them for?
The primary use for our third-party integrations are to:
Sync membership between teams channels and Chezie - WorkOS.
Push notifications for new events and group updates.
Track engagement within a Slack/Teams channel (if possible).
Allow users to push notifications to a Slack/Teams channel (if possible).
Our use cases for our integrations will expand. There will be no blind scraping of user data but targeted ephemeral and in some instances stored data to reference associations between user’s, ERGs, events, and teams. The principal goal behind our third-party integrations is to boost user engagement by making Chezie functions accessible outside of the Chezie site.
How do you gain access to our data?
If you use Chezie’s third-party integration the installer of integration will give Chezie permission to access cursory user data that is then used to make the user’s experience with Chezie a lot more seamless. The data Chezie’s integration will access is limited, targeted and gained through secure APIs.
This process is referred to as OAuth 2.0 authorization code grant flow and it is the industry standard for accessing APIs.
Slack Integration
Provided are details on Chezie’s Slack Integration:
User role to install app
Account admin(s)
Permissions
On behalf of users, Chezie can:
View information about a user’s identity, granted by 1 team member (admin)
On behalf of the app, Chezie can:
Send messages as @chezie
View basic information about public channels in a workspace
Send messages as @chezie with a customized username and avatar
View messages and other content in public channels that Chezie has been added to
View messages and other content in private channels that Chezie has been added to
View messages and other content in direct messages that Chezie has been added to
View messages and other content in group direct messages that Chezie has been added to
View basic information about private channels that Chezie has been added to
View people in a workspace
View email addresses of people in a workspace </aside>
<aside> 💡 Scopes
Bot Token Scopes - Click on scope for a detailed overview of their access.
User Token Scopes
Google Calendar Integration
Provided are details on Chezie’s Google Integration:
User role to install app
Account admin(s)
Permissions
On behalf of the app, Chezie can:
View information about a user’s identity, granted by 1 team member (admin)
On behalf of the app, Chezie can:
See your primary Google Account email address
See your personal info, including any personal information you’ve made publicly available.
View events on all your calendars
Associate you with your personal information on Google
View calendar settings
See, edit, share, and permanently delete all calendars you can access using Google Calendar
Scopes
Click on scope for a detailed overview of their access.
Microsoft Chat Integration
Provided are details on Chezie’s Microsoft Integration - Chat:
User role to install app
Account admin(s)
Permissions
On behalf of users, Chezie can:
Send channel messages in Microsoft Teams
On behalf of the app, Chezie can:
View a user’s display name, given name, job title, office location, email, surname.
Retrieve the properties and relationships of a profile object for a given user. Properties include user ID. Relationships include, accounts, anniversaries, interests, interests, positions. A full list of relationships can be viewed here.
Create groups and read all group properties and memberships on behalf of the signed-in user. Additionally allows group owners to manage their groups and allows group members to update group content.
Create groups and read all group properties and memberships on behalf of the signed-in user. Additionally allows group owners to manage their groups and allows group members to update group content.
List groups, and to read their properties and all group memberships on behalf of the signed-in user. Also allows the app to read calendar, conversations, files, and other group content for all groups the signed-in user can access.
Scopes
Click on scope for a detailed overview of their access.
Microsoft Teams Integration - Video
Provided are details on Chezie’s Microsoft Integration Video:
User role to install app
Account admin(s)
Permissions
On behalf of the app, Chezie can:
Retrieve the properties and relationships of a profile object for a given user. Properties include user ID. Relationships include, accounts, anniversaries, interests, interests, positions. A full list of relationships can be viewed here.
View a user’s display name, given name, job title, office location, email, surname.
Delete a profile object
Create a Microsoft event.
Maintain access to data you have given it access to.
All of the aforementioned data.
Scopes
Click on scope for a detailed overview of their access.
Outlook Calendar Integration
Provided are details on Chezie’s Microsoft Integration - Outlook Calendar:
User role to install app
Account admin(s)
Permissions
On behalf of users, Chezie can:
Have full access to user calendars.
Used to create calendar events associated with Teams Event.
Can readily view, read, update and delete calendar events.
Specify time zones in event creation.
Create a CalendarGroup
Get the free/busy availability information for a collection of users, distributions lists, or resources, for a specified time period.
Full list of functionality granted here.
On behalf of the app, Chezie can:
Access to calendar(s). Create, read, update, delete calendar events.
View a user’s display name, given name, job title, office location, email, surname.
Suggest meeting times and locations based on organizer and attendee availability and time or location constraints.
Retrieve the properties and relationships of a profile object for a given user. Properties include user ID. Relationships include, accounts, anniversaries, interests, interests, positions. A full list of relationships can be viewed here.
Zoom Integration
Provided are details on Chezie’s Zoom Integration:
User role to install app
Account admin(s)
Permissions
On behalf of users, Chezie can:
View Settings and preferences.
View Profile and Contact Information.
View and access to calendar of scheduled Zoom meetings and webinars.
Registration information relevant to a Zoom meetings - name, contact info., responses.
Content generated in Zoom products may include invite details, poll data, meeting name.
Participant profile, name, display name, email, phone number, user ID, other information.
On behalf of the app, Chezie can:
Manage registration information, which may include scheduling Zoom experiences or adding or deleting registrants.
Manage participants, which may include assigning participants to specific breakout rooms and specifying an interpreter for the session.
Manage content and information generated in the context of Zoom experiences, which may include audio, video, messages, meeting or chat name, agenda, transcriptions, and responses to polls and Q&A.
Scopes
Click on scope for a detailed overview of their access.
Password Policy
General
Generally our password policy dictates that we don’t use birthdays, anniversaries, or dates of noteworthiness that someone would be able to associate with employees through personal research. Long form passwords should be at least 12 characters in length and include symbols, numbers, upper and lower case letters.
Our core team and stakeholders with access or exposure to sensitive information use password managers to handle password generation/storage for all Chezie related services.
Technical details of password generation and management are as follows:
Passwords are randomly generated and over 12 characters in length.
Master passwords should be at least 12 characters in length and include symbols, numbers, upper and lower case letters.
All Chezie employees are required to install and use Dashlane for secure password storage.
Devices
Computers
Passwords should be at least 12 characters in length and include symbols, numbers, upper and lower case letters. Passwords should not reference birthday or anniversary information.
Mobile Devices
Mobile devices should be protected by a password at least 6 characters in length and should not reference birthday or anniversary information. Screen should lock immediately or after a short time (no more than 5 minutes) of inactivity.
Cloud
DigitalOcean
DigitalOcean password is password manager generated and maintained. MFA is implemented for access into our DigitalOcean services.
Incident Management Program
General
We define an incident as anything that degrades a client’s user experience in such a way that they are not able to use our service. Our response is critical to ensuring our momentum moves forward and our users are able to use Chezie without any hindrances.
The use cases considered are mainly service outages but an incident can really be a number of things. We give team members the latitude to label something an incident but they must follow some guidelines:
Be consistent with incident labeling. Although we will not put a lid on incidents, not everything should be considered an incident.
Consider how different stakeholders will help with the incident and have everyone execute their identified function.
Team members are required to fill out a form of incident details.
There is a post mortem that the team should be part of. Discuss and examine why the incident happened and how it can be avoided in the future.
Tools of the trade
Issue tracking - Every issue will be tracked using Linear. The issue(s) will be transparent and tracked until resolution (completed).
Google Meet - Real time communication and interfacing will help identify issues.
Notion - We use Notion to detail incidents/issues and share postmortems.
Slack/Teams/Email - Communicating status with customers will help keep everyone informed.
Incident Manager
Every incident will have an incident manager (IM). The incident manager is a role and they are empowered to take any action necessary to resolve the incident. The IM can call, message, and contact anyone in the company to ensure the resolution of the incident is swift. We define roles during an incident because incidents have range so we leverage whoever best fits certain roles to ensure efficient success.
Incident Table
Following is filled for every incident:
Fill out Notion doc with above details ☝🏽
Assessing the incident
After we’ve established communication, it’s time to assess the incident.
Things to consider:
What is the extent of business impact?
What is the customer experience like?
Who is affected?
When did the incident begin?
How many support cases have customers opened?
As we assess, we will record data in our Notion Incident Document to gather as much data as possible and so that visibility is company wide. Our Incident Document will be our single source of truth.
Based on the business impact of the incident we will assign a severity level to it. We have 4 different levels of severity
Establish the severity of the incident and report it to the team. An urgent incident is essentially all hands on deck immediately. Medium and low do not require as many resources but get bumped to the top of our TODO list.
Raise a new issue
Create an issue in Linear that addresses all of the above. Assign issue to Incident Manager.
Communication
It’s clear the incident is real, you want to communicate internally and externally as soon as you can.
Internal communication is to reduce confusion and optimize clarity in order to respond ASAP.
The goal of external communication is to let the customer know you know something is wrong and that you’re looking to fix the incident as soon as possible.
Communication is important for both your team members and customers, this kind of transparency breeds trust in all parties. After all, we follow best practices, and always have our customer's best interest in mind.
We will use Slack/Teams and email as our external/internal communication tools.
We will send follow ups at every stage of the incident management process until resolution is reached.
Delegation
The IM will delegate roles that best fit team members.
Team members will be responsible and responsive, as long as the role is clear, they will be able to work quickly as part of the incident team.
Our roles are:
Incident Manager - Varies
Tech Lead - Varies
Senior technical responder. Responsible for identifying what’s broken and why. Will also be responsible for implementing changes and running the tech team. Works in conjunction with IM.
Communications Manager - Dumebi
A person familiar with public communications. Should be our company’s communications point of contact. Responsible for writing and sending communications to all stakeholders.
Review and Resolve
We’ve figured out what the issue is. Time for resolution.
Watch for team fatigue.
Ensure team members are focusing on issues at hand and that resolution is imminent.
If it’s a long night, consider rotating roles. Who has been working the longest, time zones to be considered.
Make sure everyone feels like they are working toward a singular and shared goal, this is no time for segmentation in thought.
When business impact has ended the incident is over.
We will fill out our Notion incident template with issues, post mortem notes. Points of interest.
Start of impact time
Detection time
Time to recover
We close out linear issues and go in depth into the post mortem in the next stand up meeting.
Privacy
Is there collection, access, processing, disclosure, or retention of any classification of personal information or personal data of individuals on behalf of the client?
Chezie will ask for targeted user data for the purpose of data aggregation and compilation of insights.
Is there a Third Party Risk Management Program (including ongoing monitoring) in place to address data protection safeguards (administrative, technical, and physical safeguards for the security of the client-scoped data?
Is there a documented policy or process to maintain accurate, complete, timely and relevant records of client-scoped data?
We maintain only data that is relevant.
All-Encompassing
Employee Onboarding
Employees are subject to background checks and confidentiality agreements.
Log Retention Policy
We have a log retention policy of 90 days. Within 90 days, all logs are readily available, and then after 90 days, logs are archived and retained for 6 years. After 6 years, all archives are destroyed.
What is client data used for?
Aggregation and Analysis. No marketing.
Appendix - Google Scope Details


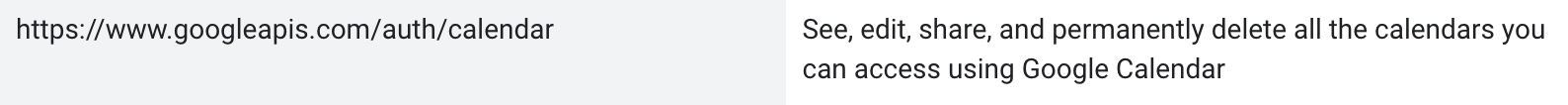

For more details regarding google scopes:
https://developers.google.com/identity/protocols/oauth2/scopes